Computer Networks – Assignment 3
Network Security [P6]
In order to demonstrate the process of securing a network router and configuring a computer and switch to create a LAN, I completed the task and documented the steps I took.
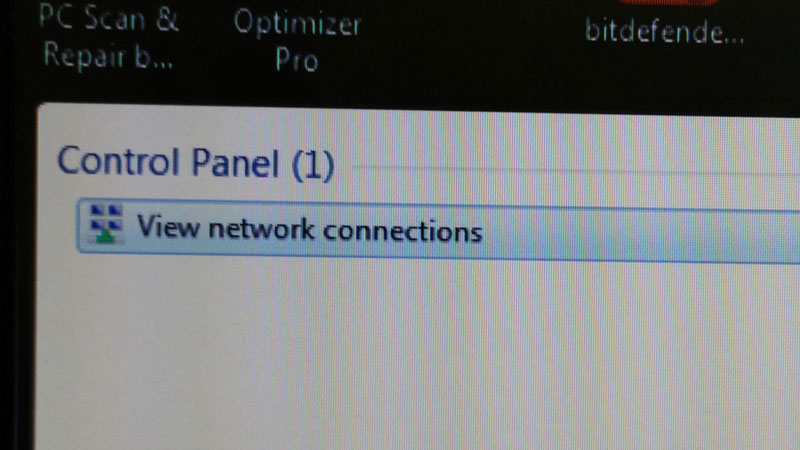 In order to access the network configuration on Windows, I searched for "network" in the start menu and picked the first and only result.
In order to access the network configuration on Windows, I searched for "network" in the start menu and picked the first and only result.
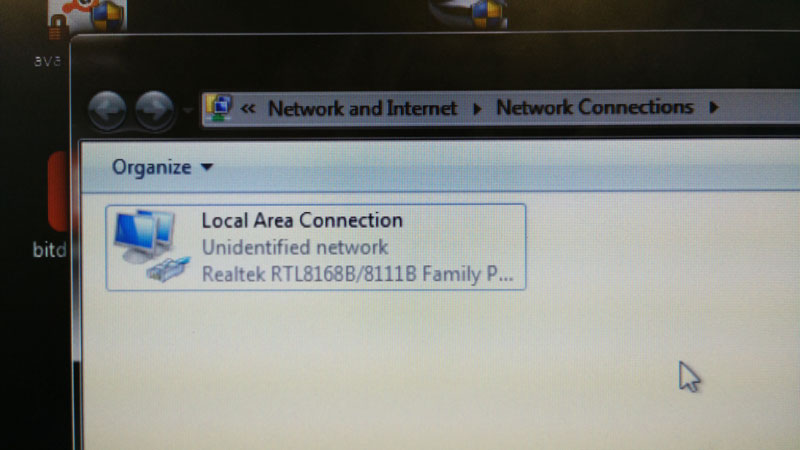 I then double-clicked the one available option, "Local Area Connection". This opened the status dialogue box for the network interface.
I then double-clicked the one available option, "Local Area Connection". This opened the status dialogue box for the network interface.
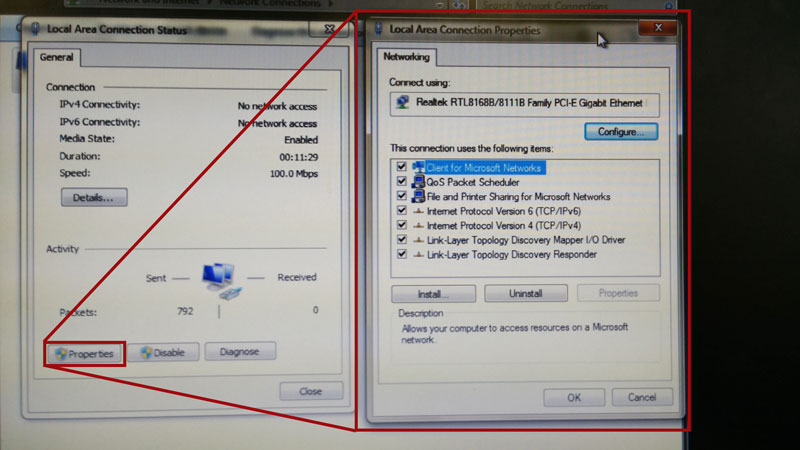 I clicked the button marked "Properties" in the status dialogue box, which opened the interface's configuration dialogue box.
I clicked the button marked "Properties" in the status dialogue box, which opened the interface's configuration dialogue box.
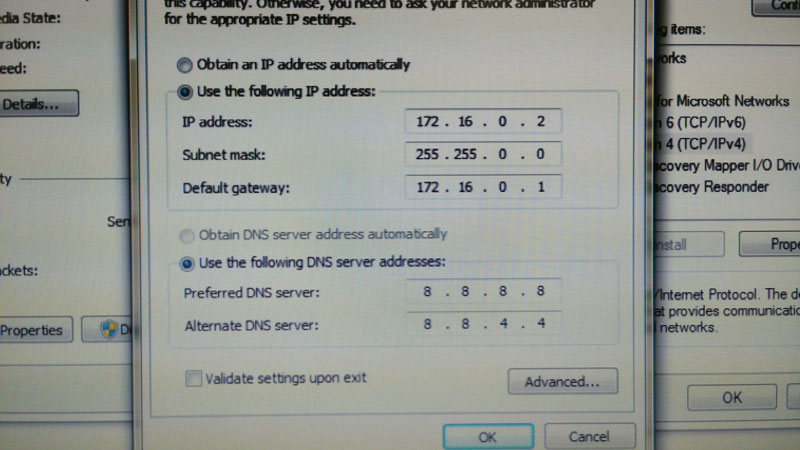 An address within the universal private range was assigned to the computer. Although not required, the IP addresses for Google's public DNS servers were included in the configuration as well.
An address within the universal private range was assigned to the computer. Although not required, the IP addresses for Google's public DNS servers were included in the configuration as well.
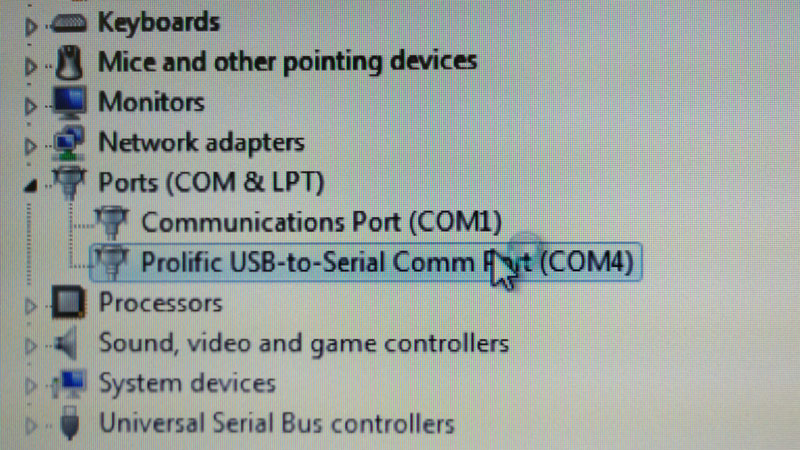 In order to connect to the router via console cable, the Windows Device Manager was used to identify which COM port the computer had detected the router on.
In order to connect to the router via console cable, the Windows Device Manager was used to identify which COM port the computer had detected the router on.
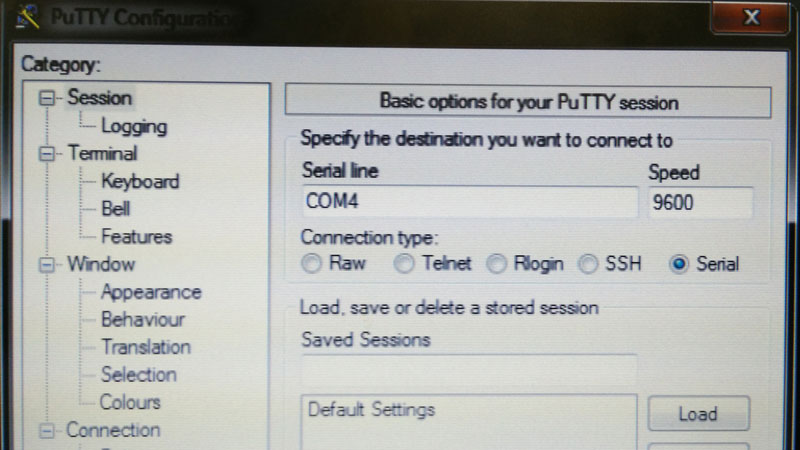 With the port number known, the router was connected to using PuTTY, a free utility for accessing remote terminals.
With the port number known, the router was connected to using PuTTY, a free utility for accessing remote terminals.
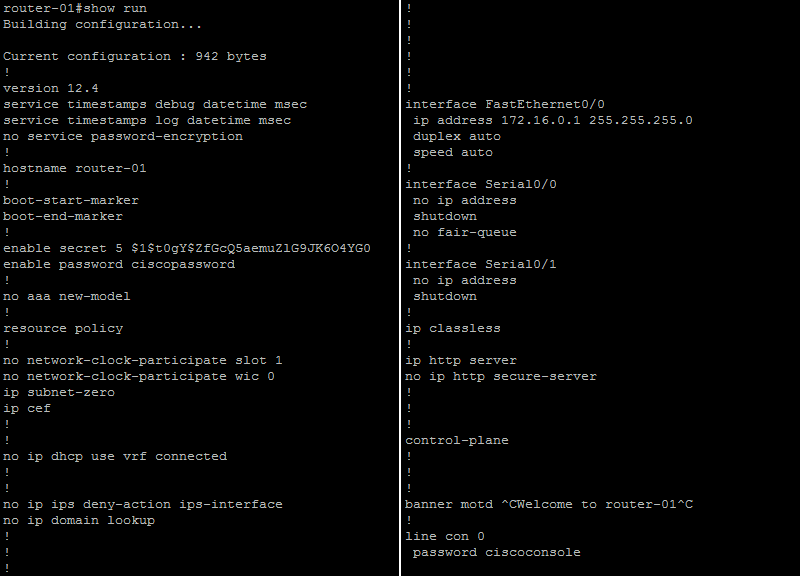 After configuration, the
After configuration, the show running-config command was used to display configuration options in use. In order for these to be used when the router were to next power on, the configuration would need to be saved.
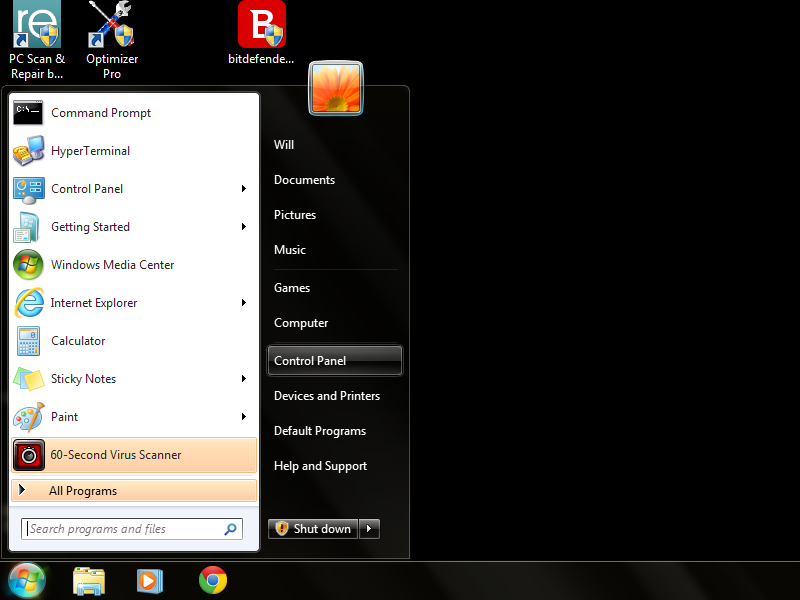 The process of uninstalling software begins with opening the Control Panel.
The process of uninstalling software begins with opening the Control Panel.
 The link to the software uninstalling area of Control Panel can be followed in order to view installed software.
The link to the software uninstalling area of Control Panel can be followed in order to view installed software.
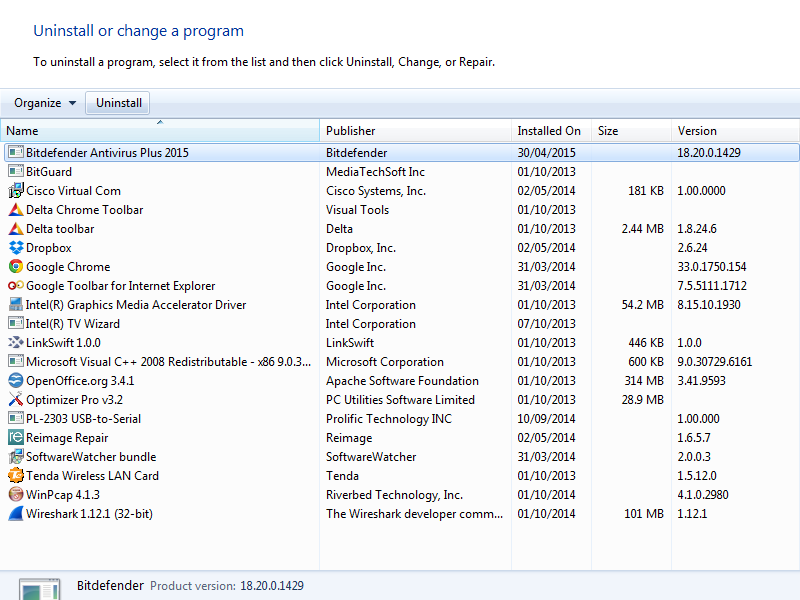 Once the list of software had populated, the program in question was selected and the button to uninstall clicked. The rest of process involved following on-screen instructions.
Once the list of software had populated, the program in question was selected and the button to uninstall clicked. The rest of process involved following on-screen instructions.
 Here the Avast installer loads. Avast (or "avast!") is a free anti-virus software package, that can be used to improve the strength of a computer system when facing digital threats.
Here the Avast installer loads. Avast (or "avast!") is a free anti-virus software package, that can be used to improve the strength of a computer system when facing digital threats.
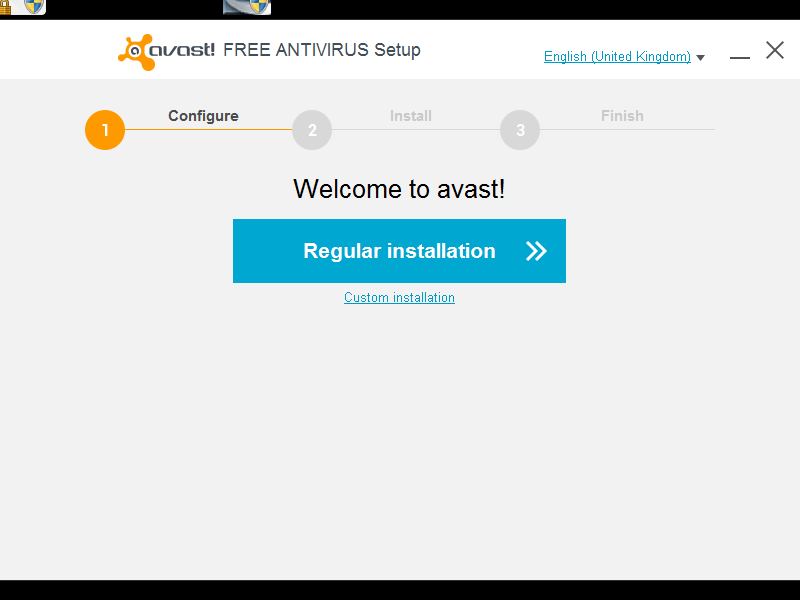 The user is given the opportunity to select a "Regular" or "Custom" installation.
The user is given the opportunity to select a "Regular" or "Custom" installation.
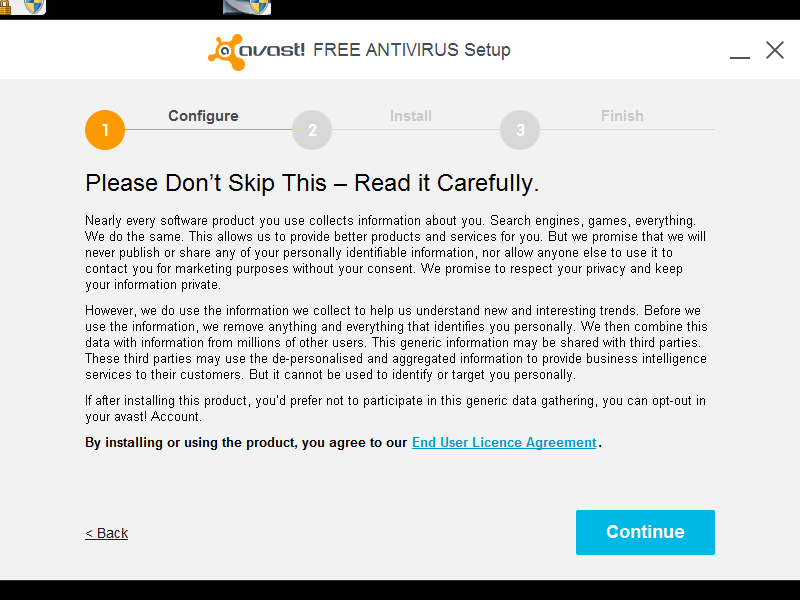 A license that must be adhered to by the user must be agreed to before the installer will continue.
A license that must be adhered to by the user must be agreed to before the installer will continue.
 The installer will then copy files, create registry entries and configure other settings for the software to install.
The installer will then copy files, create registry entries and configure other settings for the software to install.
 Once the installation process has a success, the user is presented with a confirmation of such.
Once the installation process has a success, the user is presented with a confirmation of such.
Importance of Security [M3]
During a time when breaching security is a thriving business, it's important to take steps to secure servers and public-facing computers, as well as codes of practice and other infrastructure. If systems are not evaluated and weaknesses identified, a network or business can be left vulnerable to attackers.
Common Threats
There are a number of prominent types of threat commonly fallen victim to by businesses. Targeted attacks may use a combination of these in order to achieve their goal.
Impact on Business
Loss of reputation is the result of almost any security breach, and is what almost all incidents boil down to. Loss of reputation will almost surely lead to a financial loss for the business in both short and long terms, and this could spell the failing of the organisation.
Financial loss is the effective result of reputational loss, and can lead to the failing of a business. Financial loss can come as the result of a loss of business and customers, but also as the result of paying fines and legal fees after particularly serious incidents.
Minimising Risk
Network Services [P5]
Networks can be used for a huge number of applications, and some of the most popular have been detailed below.
Communication
Perhaps the most common use of computer networks is communication between users. Hundreds of different protocols and applications have been built over the years to facilitate communication in a number of different forms. Among the more popular protocols are IMAP, POP and SMTP (email); IRC and XMPP (instant messaging); and HTTP(S) (world wide web).
These protocols must be implemented in pieces to software in order to be used. When running a Linux server stack, one can use Postfix and Dovecot as SMTP and IMAP/POP servers, facilitating the sending and receiving of email. Users of the Microsoft ecosystem often use the proprietary Exchange protocol – replacing SMTP, IMAP and POP – which also provides conventional protocol interfaces for clients that do not support Exchange.
Remote Access
Networks can also be used to offer remote desktop or other remote access services. The SSH protocol, for example, is often used to gain terminal access to a server or other networked device, which is useful for configuration and management of network infrastructure.
The remote desktop protocol, or RDP, allows one to control another computer graphically. Using Remote Desktop Connection in Windows, one can connect to another machine, granted that it's switched on, and then be shown a real-time view of that computer's desktop. When using Linux, VNC can be used to connect to an X display server running on the remote device. Data from keyboards, mice, microphones and other input devices is forwarded to the remote device, allowing the user to use it as though the connection was direct. This is particularly useful for employees who need to access their computers at their office from out in the field or from home. It's also convenient for server administration, as servers are rarely connected to a monitor or other human interface devices, although servers are more commonly managed using a command line.
File Services
The copying and moving of files between different systems is a very common need within corporate networks and across the internet. Many protocols have been designed to allow the transfer of files, commonly in both directions. In the case of SFTP, the protocol implements a client–server model, whereas BitTorrent is an example of a peer-to-peer protocol.
SFTP
Using an SSH connection to wrap and encrypt the content transferred between computers, SFTP is more secure alternative to FTP. The use of SFTP is almost identical to the use of FTP, save for the fact that the client must be capable of public-private key encryption and potentially authentication (as key pairs can be used rather than usernames and passwords).
SFTP is an implementation of the client–server model. Server software running on one machine listens for requests originating from a compatible client program on another machine.
BitTorrent
When using SFTP, a file is transferred between a pair of hosts. One of the two machines acts as the server, whether or not it's comprised of server hardware, and runs software that listens for incoming traffic on the right port. BitTorrent file transfers implement a completely different data flow model, distributing the content among a swarm of peers. Every client that wishes to gain a copy of the file will connect to the swarm and request the file from the other clients. As the file downloads, with different parts of the file being received from different peers in the swarm, the client will be able to start uploading the file again to new peers that have joined.
When a peer first joins the swarm and requests the file it is referred to as a leecher, but once the peer begins to upload content to other peers it is referred to as a seed. Torrents with a high number of seeders and a relatively low number of leechers are preferable when choosing a swarm to join as there is a higher chance of gaining a copy of the file. It's considered ill-mannered to download a file and leave the swarm before allowing it to seed first. One should instead wait until the amount of data uploaded matches or exceeds that downloaded; until one has a positive ratio. If people leech the file and leave without seeding, the health of a torrent – its contents' availability – is reduced, and sometimes to such a degree that the content cannot be downloaded.
Although often associated with piracy, the BitTorrent file sharing protocol is perfectly legal itself. The Linux community makes extensive use of the protocol, for instance, in the distribution of operating system disc images. The use of the protocol means that the load is taken off of servers, and files can be downloaded quicker by people requiring a copy. This decentralised model of file transfer suits mass transfer of content to a number of recipients, whereas SFTP is better suited to smaller one-time transfer to a specific machine.
Application Services
Desktop and web applications can be installed on a server and accessed by clients as and when required. This makes the process of upgrading a piece of software on a network much easier, and means that applications can effectively be added to a group of computers with almost no delay.
An example of a network being used to provide access to an application can be found with the Moodle educational content/course management system (CMS). The software is freely distributed and used by a number of educational institutions, having been written in PHP. Using the CMS on a webserver and integrating the software with databases and file storage infrastructure allows for students and faculty to easily manage learning resources and assignment deadlines. The software is accessed using a web browser which will connect to the webserver using the HTTP and HTTPS protocols. The nature of this method of accessing software means that with minimal extra work, the CMS can be made accessible outside of an organisation's or institution's intranet and via the world wide web. By employing the right security practices, this can be made perfectly secure, and makes working outside of hours easier for students and faculty.
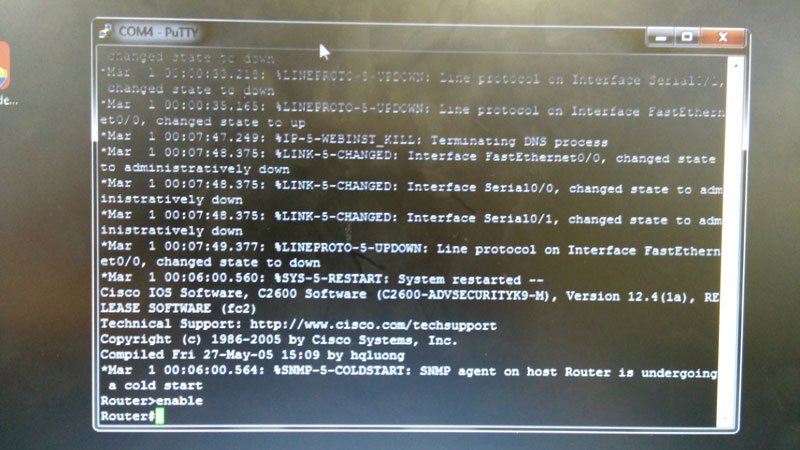 The
The