Installing and Upgrading Software – Assignment 2
Planning Stage [P3]
Installation
- Software for new install: LibreOffice suite
| Stage | Notes | Completed |
|---|---|---|
| Prerequisites | Before the installation process begins I will check that the computer has a working connection to the internet. | |
| Communication with other parties | In a real scenario, I would double-check that those who had requested the installation were certain of their decision. | |
| User privileges | In order perform the installation I will root user privileges, most easily obtained using the sudo program. I will therefore need access to an account trusted by sudo; likely an administration account. |
|
| Guidance for colleagues | The new software will appear in the menu alongside the other installed software. Each program will be available under its respective category, which is most commonly "office". Licence information regarding LibreOffice can be read online (www.libreoffice.org). | |
| Installation documentation | I will look online at the LibreOffice Git repository for an installation README, as well as the Launchpad project page for any recently discovered issues. I will make license information available to users. | |
| Loading facilities | The software installation will be downloaded during the process of installation. Using a package repository mirror on the network server, the packages will not need to be downloaded from the internet for each client, but rather just copied from another device on the network. Package repository mirrors can be easily set up, and clients can easily be configured to use one. As the data is originating from a server, the speed will depend on how quickly the server can load the data itself, although this could be very quick with the use of RAM disc. |
Upgrade
- Software for upgrade: VLC Media Player
| Stage | Notes | Completed |
|---|---|---|
| Prerequisites | The updating process will require a working internet connection as well. | |
| Communication with other parties | I would not seek confirmation before upgrading as I would when installing new software as I would not expect any objection from employees. Also, unless objection was widespread and opinions could not be changed, I would still go ahead. | |
| User privileges | The upgrade process requires the same permissions as the installation process, detailed above. | |
| Guidance for colleagues | The software in question, VLC media player, and any other packages which are out of date will now be upgraded to the latest stable release version. This process should be seamless, and the new software should be available very soon. | |
| Installation documentation | I would look online at the Ubuntu package database to check that no obvious errors had cropped up. The likelihood of such an event is low, and faulty versions of a software package would not be made available to the public. | |
| Loading facilities | As with the new installation of LibreOffice, the VLC media player upgrade would only require fetching the update from a local server. See the installation plan table for more information. |
Installation Report [P4]
Below are images showing the key stages of the installation process, with Ubuntu Linux used to demonstrate. The process would be same using Debian Linux, as the former is based on the latter, and the two use the same package management program.
 One can run
One can run apt-cache search libreoffice to list packages with "libreoffice" in their name or short description. This is very rarely necessary when finding a package.
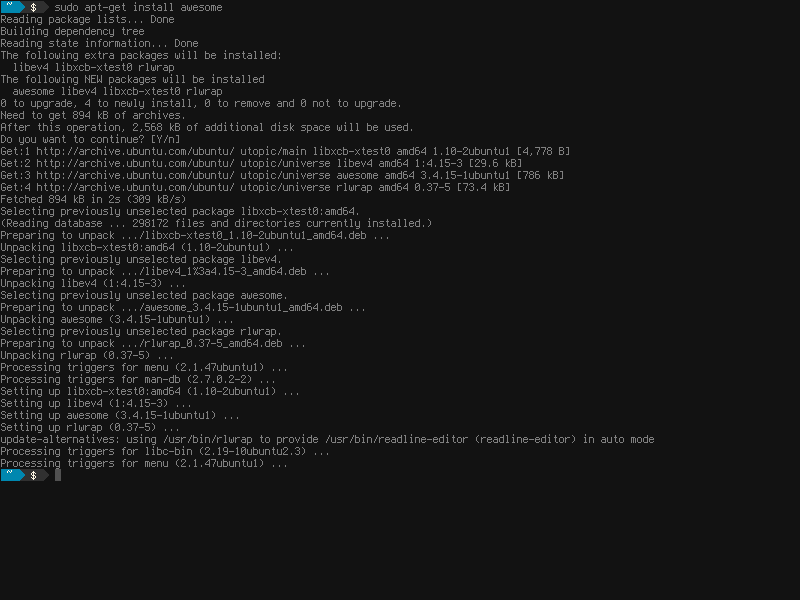 As LibreOffice was already installed, I decided to demonstrate the installation with AwesomeWM, a popular tiling window manager. The package is installed by running
As LibreOffice was already installed, I decided to demonstrate the installation with AwesomeWM, a popular tiling window manager. The package is installed by running apt-get install awesome, and LibreOffice would be installed with apt-get install libreoffice.
Upgrade Report [P5]
Below are images showing the key stages of the software upgrade process. Ubuntu Linux is once again used.
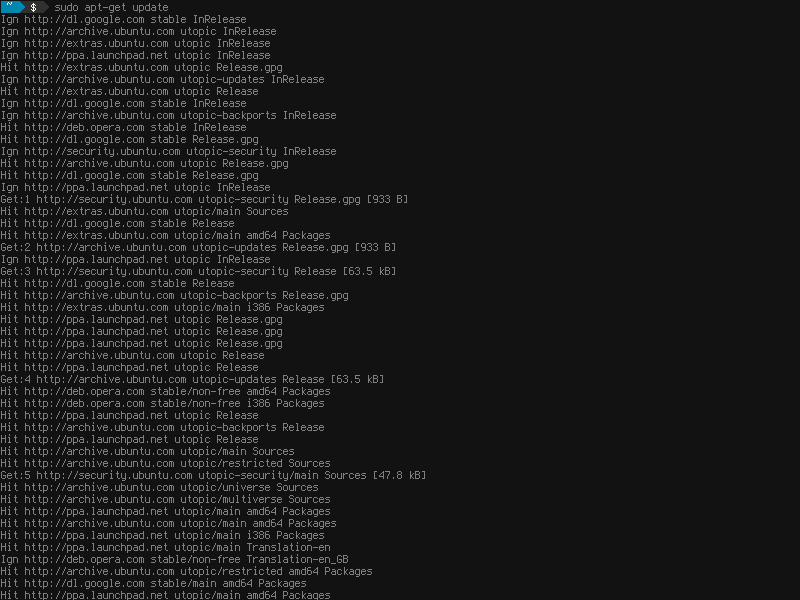 When upgrading, one must first refresh the local APT package database with
When upgrading, one must first refresh the local APT package database with apt-get update. This makes the computer aware of new package releases and changes to package metadata.
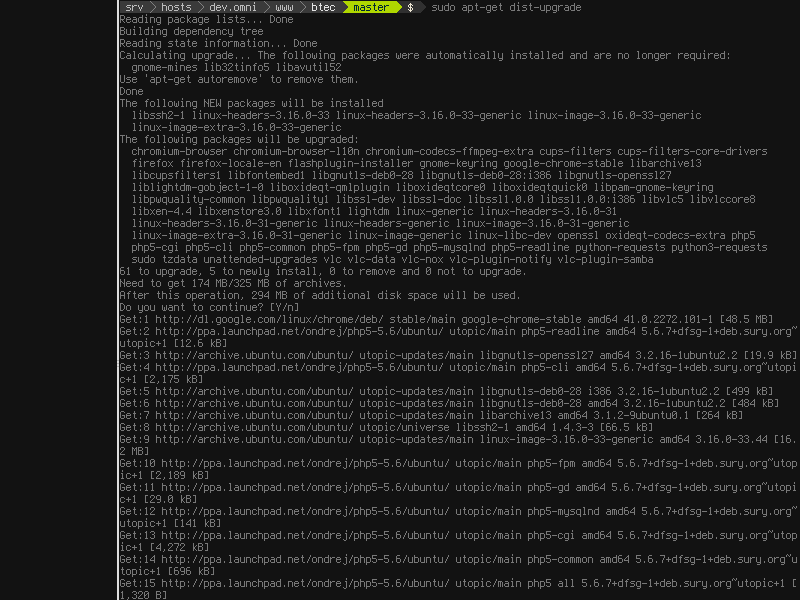 Once the database is updated, one can simply run
Once the database is updated, one can simply run apt-get dist-upgrade to upgrade all packages to their latest versions. The "dist-" part of the command means that the upgrade process may upgrade the entire OS to a newer version. In rolling release distributions (distros) such as Arch Linux, all packages being up-to-date means the entire OS is up-to-date; there are no separated releases as there are with Debian Linux or OS X.
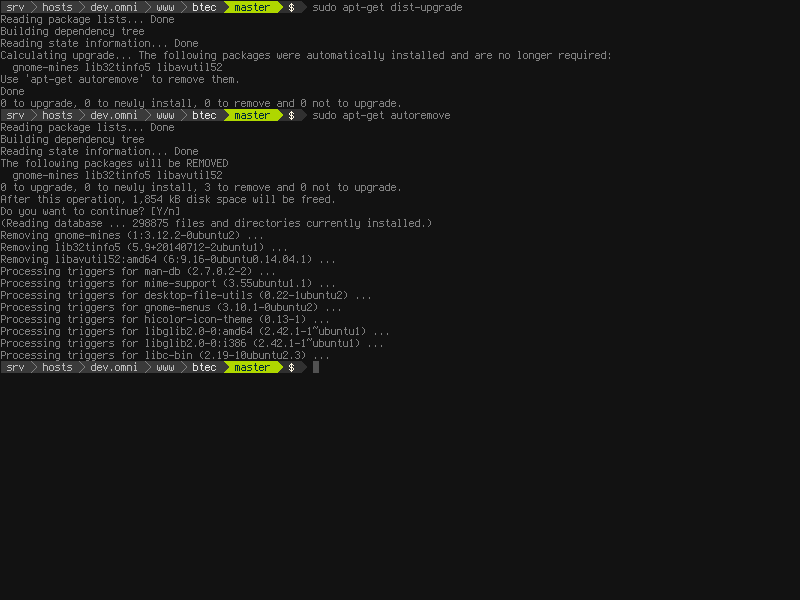 If no updates are available for download,
If no updates are available for download, apt-get will exit after showing information about the packages installed. For example, packages that were installed automatically but are no longer depended upon by any other packages will be listed, and can be removed with the autoremove option.
Requirements in Preparation [M2]
When installing a new package of software in Linux, and particularly across a network of computers, a few steps must be undertaken before the process can commence. In the case of a business which operates a number of employee terminals around an office, the local server mirror of the package repository will need to updated, or created if it does not exist. Using a local mirror will greatly improve the time that the process takes, will hugely reduce the stress placed on the business' internet connection, and will place less stress on the official, public package repositories. The updating process should not be more complex than running a handful of commands once the mirror has been created, which will instruct the server to download compressed archives for the latest versions of specified packages. In this case this will be the libreoffice meta-package and all of its dependencies.
My suggestion would be to perform the upgrade after work has finished on a Wednesday or Thursday; when employees are no longer using their terminals. This way the computers are not in use and can easily be worked on, and the employees are still given some time during the week to become acquainted with the new software. If the installation was performed before the weekend, employees may spend longer learning to use the new software, and more time is at risk if the upgrade is performed at the beginning of the week.
Users and management should be informed of the changes, and be prepared for potential issues that may arise, however unlikely. If users are aware of the new installation, they will be less surprised to find the new software and may even have time to practice with it outside of work. Management should also be aware of the installation so that it has a better understanding of the current events in the business' IT infrastructure.
Before proceeding with the installation, one must be familiar with potential back-out procedures if the installation process does not go accordingly to plan. In the case of Linux, one should be aware of how to remove a particular package and the packages installed alongside it, and then remove any "orphaned" packages that are not required by any other software. Removal of a package and its unneeded dependencies is outlined in the Backing Out of a Software Upgrade section.
Before being able to perform and installation, one must be able to acquire root privileges on the machines in question. This is most often achieved using the sudo command, short for "substitute user do", which allows one user to easily execute a program as another user. In order to gain root access via sudo, however, one needs access to an administration account which is trusted by sudo. Once access to an administrator user account has been granted, one is able to also access a root-level command line shell for more complex tasks which require heightened permissions.
Data Integrity when Upgrading [M3]
When performing an update of software, it's important that user data and configuration is not lost in the process. For this reason, most IT departments in businesses, organisations and institutions choose to make frequent back-ups of huge amounts of data, so that in the event of any slight mishap, everything can be recovered.
Although more or less important information may be backed up more or less often, back-ups of a system are often performed on a nightly basis. The filesystem on one drive or drive array is copied to another so that in the event of data loss or drive failure the information can be recovered. On occasion an error is made by someone on the filesystem and the issue is not noticed for several days, and this is usually accounted for. Rather than storing a single back-up of the system at once, administrators often keep every daily back-up spanning the preceding two weeks. In addition, the back-ups from every third day may be kept for the two weeks before that, and weekly backups kept for months. By keeping so many back-ups, which may seem irrelevant or over-compensative, redundancy is introduced to the system. Almost any failure recognised within around a month can be recovered from, and the majority of infrastructure can be recovered from even older back-ups.
Backing Up the Window Registry
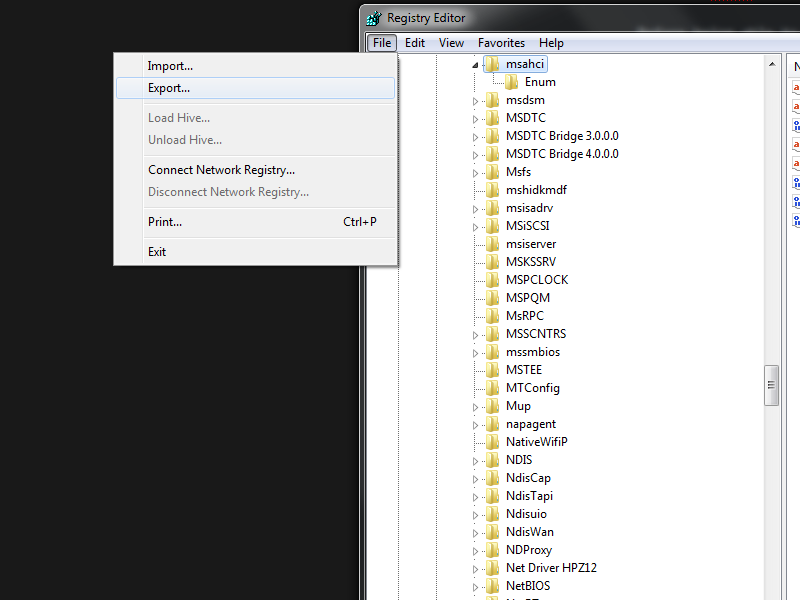 The Registry Editor, commonly known as "reg. edit.", allows the registry to be exported quickly and easily.
The Registry Editor, commonly known as "reg. edit.", allows the registry to be exported quickly and easily.
Windows uses the registry to store key-value pairs for a great amount of uses. Changes made to a Windows system's configuration are kept in the registry, which can also be edited manually with the Registry Editor, or regedit.exe. Microsoft encourages developers of software for Windows to use the registry to store information about configuration as well, which can lead to problems. When an installer program has access to administrative permissions and the registry, the potential to intentionally cause damage is real.
In order to at least partially neutralise the risk of system corruption and data loss, backups of the registry can be made. The settings in the registry can be exported using the Registry Editor, as shown above, to a new file. This file can be moved to an external storage device, uploaded to private web-based or cloud storage, copied to another partition on the drive, or placed in another safe location. This means that if a software installation or upgrade, or any other major change to the operating system, causes issues to spring up, the file can be re-imported with the registry editor into use. The export and import functionality of the Registry Editor can even be used, to an extent, to perfectly duplicate the settings of one computer to another. This is not advisable, however, as the slightest differences in hardware versions and other software can cause issues and system instability.
Windows Restore Points
In Windows, one can create snapshots of the OS and software configuration present on the computer and revert the computer to the state it was in when one was made at a later date. Restore points can be made manually before executing a strenuous or somewhat dangerous task on a computer, meaning that most issues which could occur will not cause the computer to become unusable and unrecoverable.
Restore points are made automatically at various points during usual Window operation, and these restore points are made visible in the Control Panel. An administrator user is able to revert the system to a previous state quickly and easily, and most often with success.
Restore points are also accurate, in that they only make a snapshot of the relevant system components. Personal directories and new files will not be changed when creating or reverting to an old restore point, and only replaceable data will be removed. A new restore point can even be created before the process of reverting to an old one, allowing for a restore to be un-done. Despite these advantages of restore points, there are some disadvantages as well.
The most prominent issue is that restore points work by backing-up data before a task is undertaken by the computer, and this fills a lot of disk space. Keeping a number of restore points available on a Windows machine will mean that the primary storage device used by it fills up. Although the default Windows configuration only allows System Restore to fill as much as 5% of a drive's volume with restore point data, this may be expanded in many situations. With a restricted restore point allocation, fewer back-ups can be made, and this means that older restore points will be deleted when new points are created. As many lightweight and small laptops, as well as the growing number of tablets running a full Windows installation, have a limited amount of storage space, restore point data could be an issue. Also, when using a desktop with a hard-disc drive, it is not recommended that a volume be filled above 80%, in a bid to avoid the negative effects of file fragmentation.
Backing Up a Data Drive
Very often user data is stored on a single physical drive. This makes the process of backing up the data by way of a disc clone much easier. When running Linux, one can use the popular drive management tool GParted, a graphical port of the parted utility, to duplicate partitions on a host of different devices. Copies can be made to the same physical device, or to another. This is explained in the Backing Out of a Software Upgrade section.
Backing Out of a Software Upgrade [M4]
In some situations one may wish to back out of a software upgrade or installation.
Cloning a Disc Partition
Before the process begins, one may wish to preserve an exact image of their hard-drive in its working state. In order to do this, separate, empty hard-drives could be formatted and the data from active drives them copied onto them exactly. This clone of the drive could be used to restore everything to its previous state immediately.
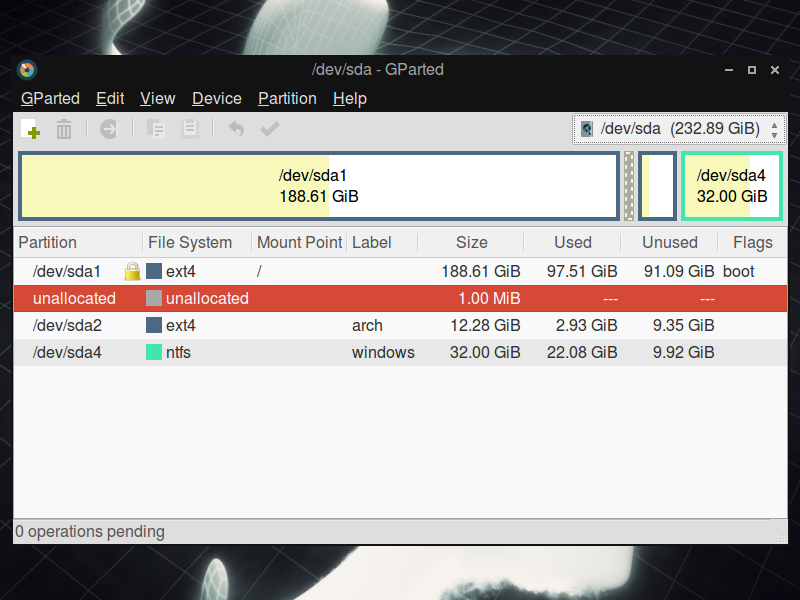 GParted, a popular drive partitioning tool for Linux, can be used to create mirrors of disc partitions. These can be copies on the same device, or on another device connected to the machine.
GParted, a popular drive partitioning tool for Linux, can be used to create mirrors of disc partitions. These can be copies on the same device, or on another device connected to the machine.
Removing Software
Most software packages install with an easy un-installation method implemented. When using a Debian based Linux distribution, the apt-get command can be used once again. The apt-get remove and apt-get purge sub-commands allow for the removal of installed packages. The former, unless used with its own --purge flag, removes the binaries and resources initially installed by the package. The latter removes this, and then removes all configuration files as well. This means that the package will behave entirely as new if ever re-installed, and some storage space will be saved.
In Windows, un-installation is usually handled directly by the program. When a program is installed, a registry entry will be created making the operating system aware of a particular executable file which can be used to remove the software. When a user opens the Control Panel and navigates to the un-installation page, Windows will show every program it's aware of. If no un-installer was supplied when the program was first installed, Windows will take the process of removal into its own hands. A typical un-installer program will remove all of the files created for the program; flush any cached data kept by the software; remove configuration data and registry entries; and and remove links to the software around the system. This is because Windows has no centralised package management system and configuration and can be performed is a great number of ways.
Backing Up the Window Registry
Creating a Windows Restore Point
Manually creating a restore point is a simple task, and one that is worth learning to complete. The easiest way to navigate to the system restore window is to search for "restore point" in the Windows Vista or higher start menu search bar. One of the first items to be returned, if not the first, will be the Control Penal option to create a new restore point. In the dialogue box that then appears, one can click Create... to make a new restore point. One will be prompted to give the restore point a recognisable name, and the back-up process will then begin. Restore points are created automatically before undergoing many complex processes, but manual restore points are still relevant.